Security: LDAP Query Mechanism
-
Mobile Web Server Authentication
LDAP Query Mechanism
LDAP Query authentication mechanism let's you configure Omniscope Mobile server to query an LDAP server to validate user credentials.- Users are stored and managed by an LDAP/Active Directory (AD) server
- Omniscope Mobile server is configured to query the LDAP/AD server
Prerequisites
To configure Omniscope Mobile server to use LDAP query mechanism you need to know the following:- LDAP distinguished name (e.g CN=Users,DC=example,DC=com)
- LDAP URL and port (e.g. LDAP://ldapserver.example.com:389)
- LDAP security authentication type (e.g. simple, or CRAM-MD5, or DIGEST-MD5, or none)
- Local domain name (e.g. example.com)
- Whether your LDAP/AD server has been configured to use your trusted certificate (only if you want to use LDAPS instead of LDAP which does not need that information)
Configuration
- Start Omniscope Mobile server
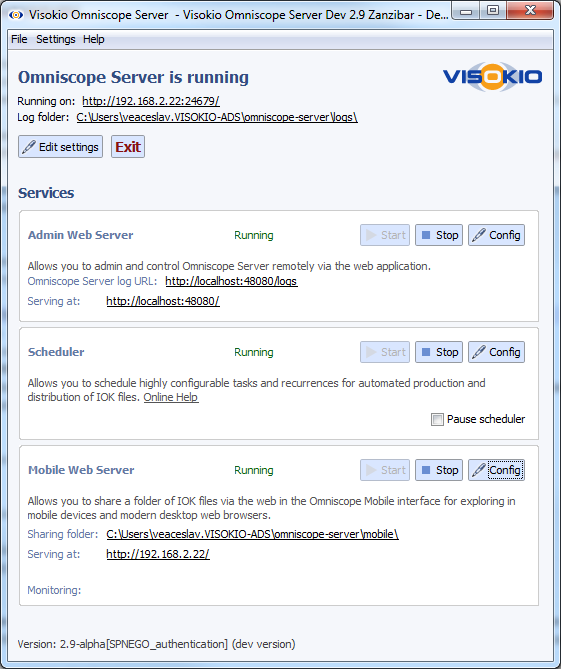
- On Mobile Web Server service section click Config, scroll down to Default folder configuration and click Edit
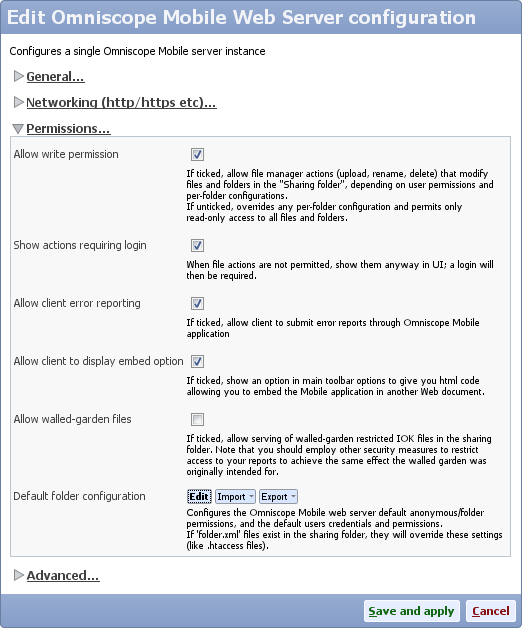
- Either create a new group with new permissions, or edit an existing group
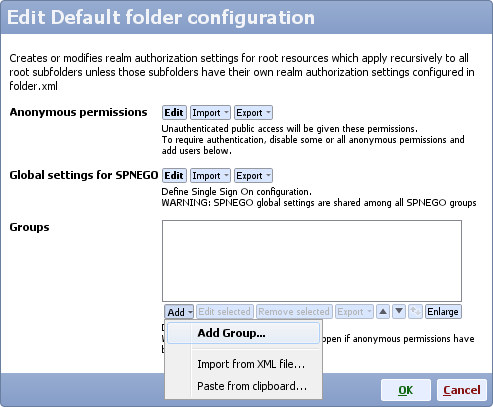
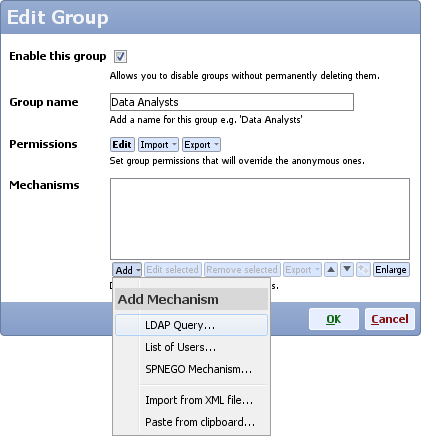
- Edit LDAP settings
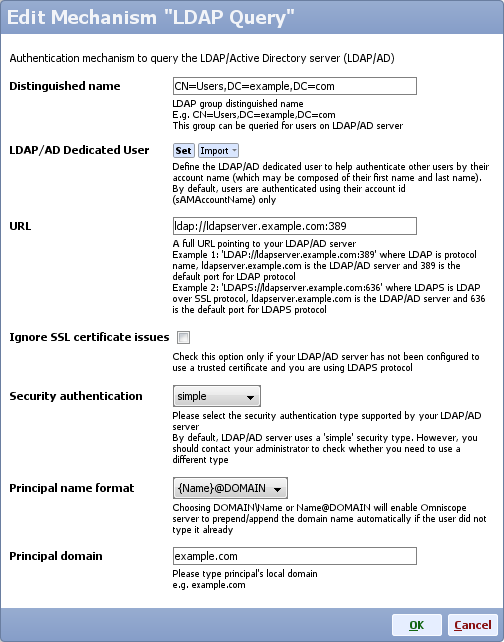
- Type LDAP distinguished name (e.g CN=Users,DC=example,DC=com), it should match the distinguished name configured on your LDAP server
- Optional: on the LDAP/AD server create a dedicated user to be used only by Omniscope Mobile server to authenticate users and add this user in the LDAP/AD Dedicated User section
Setting a dedicated user will help authenticate other users by their account name (which may be composed of their first name and last name). By default, users are authenticated using their account id (sAMAccountName) only - Type LDAP URL
This is a full URL pointing to your LDAP/AD server
Example 1: 'LDAP://ldapserver.example.com:389' where LDAP is protocol name, ldapserver.example.com is the LDAP/AD server and 389 is the default port for the LDAP protocol
Example 2: 'LDAPS://ldapserver.example.com:636' where LDAPS is LDAP over SSL protocol, ldapserver.example.com is the LDAP/AD server and 636 is the default port for the LDAPS protocol - Check Ignore Ssl certificate issues only if necessary (your LDAP/AD server has not been configured to use your trusted certificate and you want to use LDAPS protocol instead of LDAP )
- Select the security authentication type supported by your LDAP/AD server.
By default, LDAP/AD server uses a 'simple' security type. However, you should contact your administrator to check whether you need to use a different type like CRAM-MD5, or DIGEST-MD5, or none - Select principal name format. Choosing DOMAIN\{Name} or {Name}@DOMAIN will enable Omniscope server to prepend/append the domain name automatically if the user did not type it already
- Type your local domain name to be appended to usernames automatically when authenticating users. This field will be disregarded if you selected {Name} for principal name format field
LDAP Filter
If you want to authorize only specific users from a LDAP group you should use the LDAP Filter option.
For instance, let's say you have a group 'CN=Sales,CN=Users,DC=example,DC=com' that has four users: john.smith, ellen.doe and two other users. However, you want to authorize only the first two users. To do so, click the LDAP Filter option and add the two users as shown below: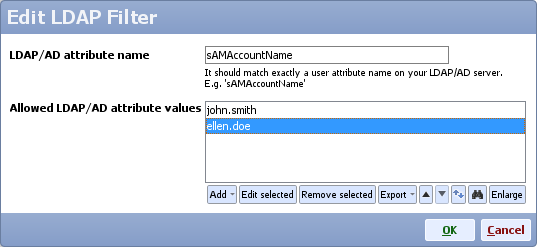
Note: The LDAP/AD attribute name should match exactly a user attribute name on your LDAP/AD server. E.g. 'sAMAccountName', and the values you add should match the actual property value for users that are authorized.
Attachments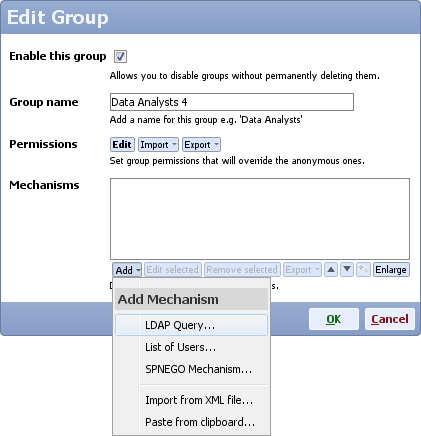
ldap_1.png 23K 
ldap_2.png 48K 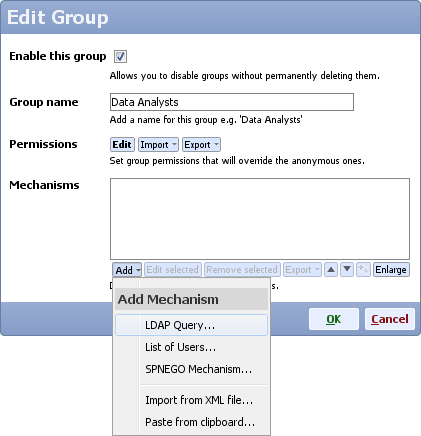
ldap_1.png 23K 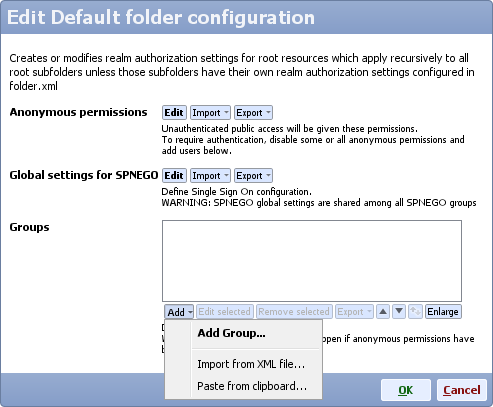
ldap_3.png 25K 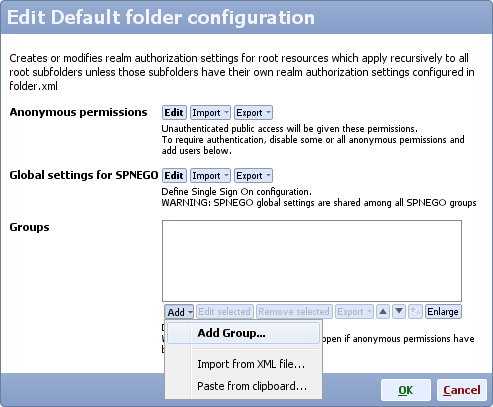
ldap_3.png 26K 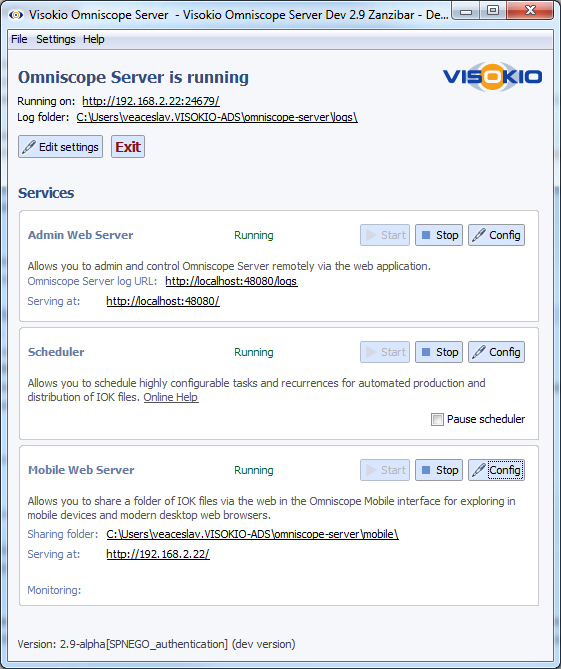
omni_1.png 67K 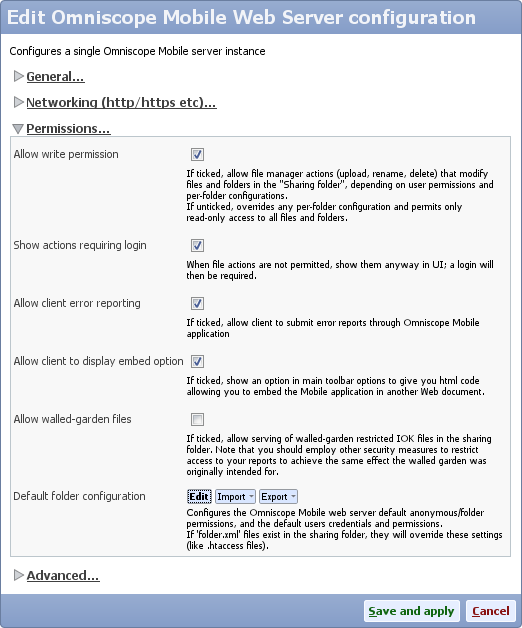
omni_2.png 46K 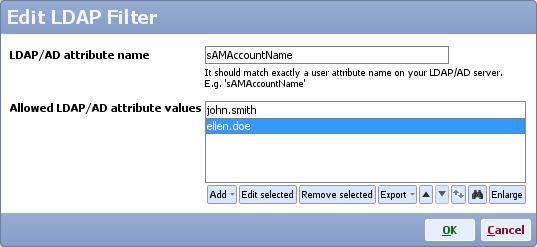
filter.png 14K
This discussion has been closed.
← All Discussions Welcome!
It looks like you're new here. If you want to get involved, click one of these buttons!
Categories
- All Discussions2,595
- General680
- Blog126
- Support1,177
- Ideas527
- Demos11
- Power tips72
- 3.0 preview2
Tagged
To send files privately to Visokio email support@visokio.com the files together with a brief description of the problem.

